How a new car is stolen without the key in under five minutes
With car theft remaining an increasing national issue, newer cars are no longer unscratched from thieves.
We wanted to see just how hands thieves could steal a new car today by engaging a locksmith to demonstrate some of the tools readily misogynist on the internet today.
We engaged Chamara, the owner of Brisbane-based Tapsy Locksmiths, to demonstrate the tools misogynist to everyone on the internet and shot a video showing how the process works.
We’re revisiting this article, which was originally published last year.
We’re not writing this story considering we want to teach people how to steal cars. All of the tools Chamara used for this experiment are legal tools that Chamara legitimately uses for his business.
However, these tools, equal to Chamara, can be purchased by virtually everyone on the internet. And you can imagine how easy it would be for these tools to fall into the wrong hands.
That’s why we’ve gone to lengths in the video to obfuscate anything that reveals the website or the tools that Chamara uses.
Background
To begin, let us provide some context. When accessing a modern automobile, one typically employs either a traditional key with a inside locking system or a proximity-sensing key, which remains in the user’s pocket while they vivify the vehicle’s lock.
In most instances, plane if a car utilizes a proximity-sensing key, a physical key is embedded within the key fob. This is to ensure transmission wangle to the vehicle if the proximity key’s shower becomes depleted. The physical keyhole may be unseen overdue a plastic tent or other decorative element.
An exception to this rule includes vehicles like Tesla, which rely solely on RFID-enabled cards or smartphones for access.
Nevertheless, Teslas are equipped with a transmission front bonnet release situated overdue the bumper in specimen the shower fails. Within the bonnet, there is a mechanism for providing power to a 12V battery, which subsequently permits hallmark with the car.
The physical key unseen within a key fob or the one used for the ignition, such as the example from the Hyundai i30, possesses a relatively distinctive cut pattern. This uniqueness, however, is not absolute, as multiple versions of the same key may exist worldwide.
Consequently, it is plausible that someone in flipside part of the globe possesses a physical key identical to yours, capable of accessing your vehicle. Nonetheless, these instances are often restricted by region, making it improbable for vehicles within your zone to share the same key profile.
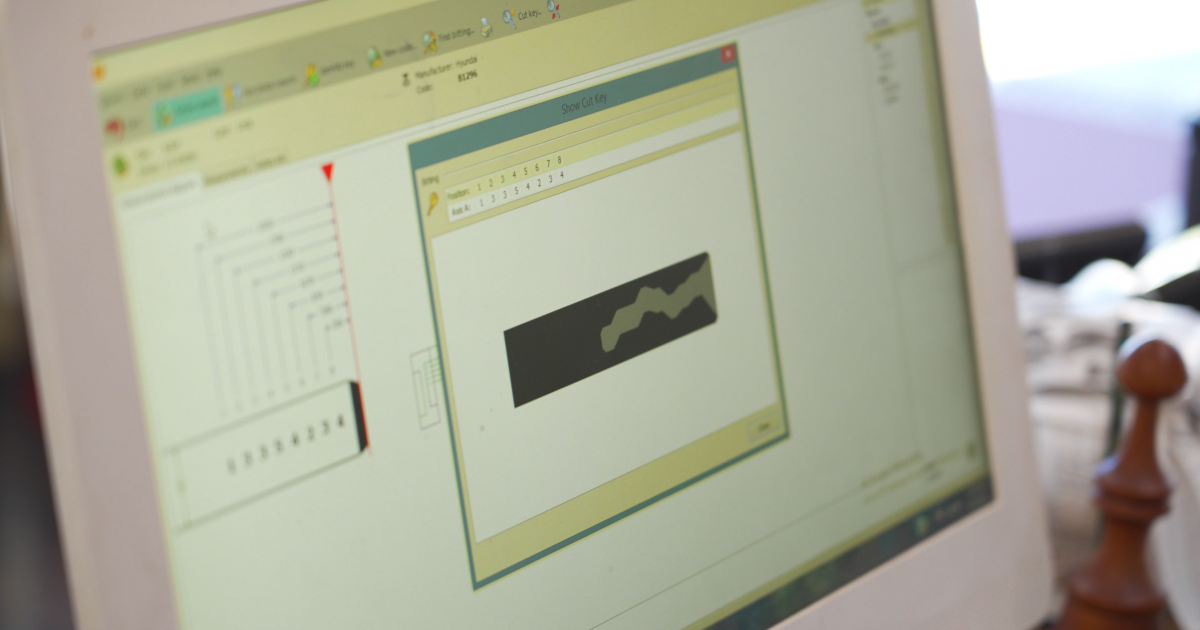
This specific key profile is prescribed a “Key Code.” Locksmiths employ this Key Lawmaking in conjunction with key wearing machines and decoding software to create an well-judged replica of the key, including its ridge profiles.
The Key Lawmaking moreover informs the locksmith of the required key type, as unrepealable keys have cuts on one side, while others full-length cuts on both sides.
Apart from the Key Code, locksmiths utilize a variety of electronic devices to encode new car keys.
The process differs among manufacturers and car brands. Some only necessitate a vital PIN code, whereas others mandate the installation of new firmware surpassing encoding a key for the vehicle.
Regardless of the method, executing this procedure outside of the manufacturer’s domain typically demands third-party hardware. Often, this hardware incorporates a decryption mechanism that utilises the vehicle’s existing algorithm to wangle the car’s electronics based on its unique Vehicle Identification Number (VIN).
Getting into the Hyundai i30
It is not uncommon for manufacturers to tuition exorbitant fees, often in the range of hundreds or plane thousands of dollars, for pure keys and programming services.
Locksmiths, such as Tapsy Locksmiths, can provide these services at a fraction of the forfeit using aftermarket or, in some instances, genuine OEM keys, which they can program themselves or instruct the consumer to program through the manufacturer.
For Hyundai vehicles specifically, it is surprisingly straightforward to both cut a new key that works in the door and program a new key within seconds of accessing the car.
Chamara demonstrated a website that, when provided with the vehicle’s VIN, generates the Key Lawmaking and PIN lawmaking for the car. While this website is ostensibly intended for locksmiths only, Chamara noted that the verification process for wangle was rather lax.
Chamara proceeded to work on an i30, utilizing the vehicle’s registration number (which could be hands obtained by a thief) to retrieve the VIN from the Queensland registration office.
After inward the VIN into the website, he obtained the Key Lawmaking and PIN code, which he used to cut a new key identical to the one in the owner’s possession.
He then proceeded to the vehicle with the electronic device required for key programming. Upon using the newly cut key to unshut the door, the watchtower was triggered. Chamara unfluctuating his electronic device to the OBD port and entered the PIN lawmaking from the website, promptly deactivating the alarm.
It is worth noting that when a car watchtower is activated, most people do not investigate immediately, typically waiting until the watchtower has persisted for a few minutes.
Chamara managed to disable the watchtower within 10 seconds of gaining wangle to the Hyundai, making it unlikely that anyone would pay sustentation to the unenduring watchtower activation.
After inward the PIN code, Chamara programmed a new key for the vehicle using a zippo key. This new key disabled the car’s immobiliser, permitting him to start the engine with the freshly cut key.
In under a minute, Chamara was worldly-wise to wangle and potentially momentum yonder in a Hyundai i30 that had been inaccessible just moments before.
Getting into the Toyota Kluger
How well-nigh a brand-new Toyota? Chamara informed us that the visitor had updated its security system in recent years.
Previously, stealing a new Toyota was as easy as stealing a Hyundai, but it became increasingly challenging with the new security measures. However, last year, the updated security system was compromised, leading to the minutiae of a third-party tool designed to shirk the system.
The procedure for the Toyota initially paralleled that of the Hyundai. First, a key for the vehicle needed to be cut, which Chamara workaday using the VIN obtained via the registration and the Queensland registration website.
Upon accessing the car using the keyhole on the door, the watchtower began to sound. Chamara then employed a variegated electronic device that connects to the OBD port and an intermediary connector linked to flipside security module. With this setup, he managed to write new firmware to the car, enabling it to recognise a zippo key as the authorised key fob.
Subsequently, he instructed the car that all existing keys were lost, and the zippo key fob communicated to the car that it was permissible to create new keys in the vehicle’s key database. After programming these new keys using the device, the car could be started and driven away.
The unshortened process took approximately 2-3 minutes. As with the previous example, the watchtower was zingy upon opening the door but was swiftly deactivated once Chamara authenticated with the car.
How to protect yourself
An increasingly prevalent method employed by thieves involves the use of relay devices.
In this approach, one thief aims the relay device at the front door of a residence, where proximity keys are often left. The device then transmits the key’s signal to an partner near the driver’s door of the vehicle. Consequently, the car perceives the key to be present, permitting the thieves to unlock and start the vehicle.
While they would be unable to restart the car without the key, the thieves could utilize one of the devices demonstrated by Chamara to reprogram a new set of keys at a remote location.
To protect versus such relay attacks, consider purchasing a small Faraday bag for storing car keys at home, which prevents the key’s signal from extending vastitude the bag’s interior lining.
In the sparsity of a website for obtaining a Key Code, criminals may resort to a turbo decoder. This tool inserts into a keyhole and, within 15 seconds, retrieves the lock’s inner key profile, enabling the thief to unlock the door as though they possessed the very key.
Once again, thieves can employ electronic devices wieldy to locksmiths to program new keys and scoot with the vehicle.
How can one prevent unauthorized wangle to the OBD port for key programming? Unfortunately, there is no simple solution. Disconnecting the OBD or disabling wangle to it entirely may provide some protection, but the OBD would be required for future mechanical diagnostics.
A increasingly constructive deterrent involves reverting to traditional security measures, such as purchasing a steering wheel lock. While a thief may succeed in programming a new key, they would be unable to steer the vehicle once it is started, thus thwarting the theft attempt.
CarExpert’s take
It is genuinely viperous to discover the ease with which a brand-new car can be stolen in today’s world. This vulnerability becomes increasingly understandable upon closer examination.
For instance, in the specimen of the Hyundai i30, which was released in 2016, the vehicle would have been in the prototype engineering phase for years prior. The security system chosen for the car may have once been a couple of years old by that time – let’s say, from 2014.
Fast forward to the present, and the security system is nearly a decade old, providing zaftig time for malicious actors to decipher the encryption and identify entry points.
A potential solution to mitigate such threats involves over-the-air security updates that can transmute the security mechanism as needed. However, this may be challenging to implement for cars relying on keys or proximity devices utilizing outdated technology.
Tesla appears to be on the right track by exclusively permitting phone or RFID wangle to their vehicles. This tideway enables the visitor to deploy security updates as vulnerabilities emerge, providing a increasingly robust defense.
Unfortunately, most legacy security systems in other vehicles on the market are substantially obsolete as soon as the cars are sold. This pressing issue warrants sustentation and whoopee to protect both consumers and manufacturers.